








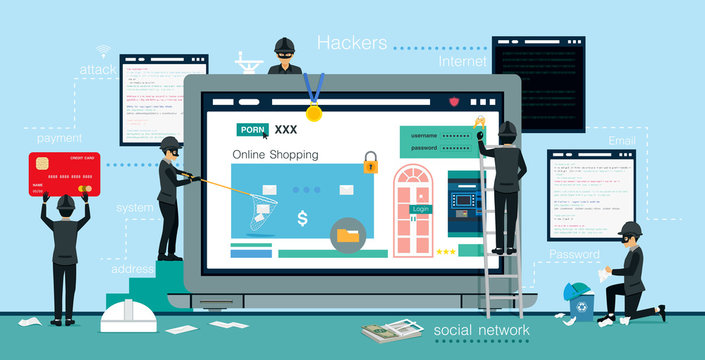






































































computer cyberspace
Wall muralscam technology online
Wall muralhacker datum phishing
Wall muralcyber crime attack
Wall muralfraud virus hacking
Wall muralnetwork business spam
Wall muralscreen alert electronic mail
Wall muralprotection threat danger
Wall muralcomputer
Wall muralcyberspace
Wall muralscam
Wall muraltechnology
Wall muralonline
Wall muralhacker
Wall muraldatum
Wall muralphishing
Wall muralcyber
Wall muralcrime
Wall muralattack
Wall muralfraud
Wall muralvirus
Wall muralhacking
Wall muralnetwork
Wall muralbusiness
Wall muralspam
Wall muralscreen
Wall muralalert
Wall muralelectronic mail
Wall muralprotection
Wall muralthreat
Wall muraldanger
Wall muralwarning
Wall muralerror
Wall mural